NACHA Banker
“Its beginning to look a lot like… fraud!
During the end of the year with Holiday celebrations, year-end activities and planning for the year ahead, it is also a good time to remind you that the fraudsters are alive and well and it’s easy to get sidetracked or to let your guard down.
And, the more technology expands, the more types of fraud there seems to be.
However, sometimes the best scams are the simplest. With this in mind, we wanted to share some information with you in a recent payment scam highlighted in an email that one of our team members’ received via their personal gmail account:
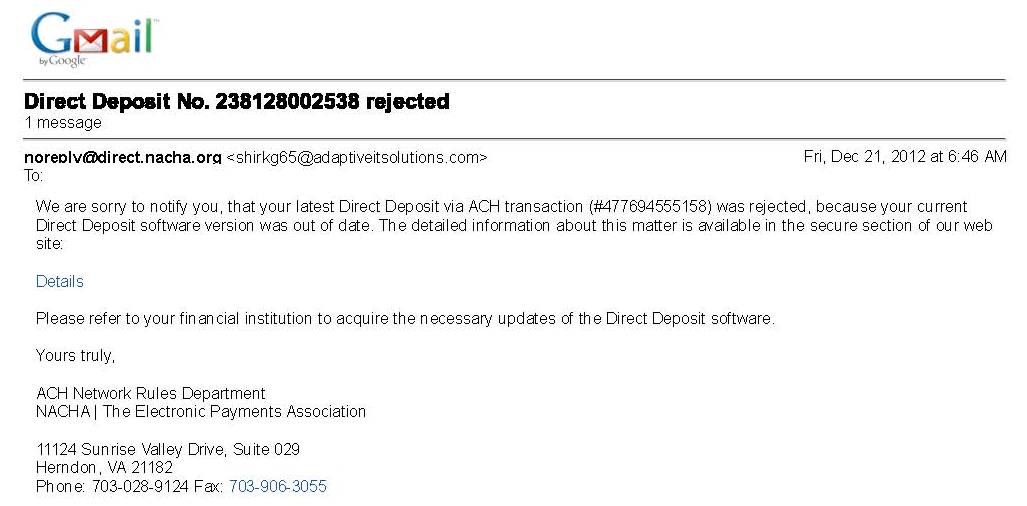
On December 21, 2012 an email was received that appeared to be from the National Automated Clearing House Association (NACHA) advising that a recent automated clearing house (ACH) deposit did not occur as expected:
Never mind the obvious part here that an individual would not be notified of a payment failure by NACHA, which is a trade association comprised of member corporations, financial institutions and vendors who serve these marketplaces with the goal of both improving and expanding the use of the ACH network as a viable means to process payments. If there were an issue with any payment transaction, the client’s financial institution would have notified the client directly and would not have done so via email – not NACHA or the Federal Reserve or some other “official body”).
However there are some other issues involved here that are noteworthy:
The email is NOT actually from NACHA. It appears to be sent via an email address of [email protected]. And while Adaptive Solutions is a real company, they would not be sending such a message on behalf of NACHA.
As a industry trade association, NACHA would have no way of knowing whether software used to transmit an ACH payment transaction file to a financial institution was proper or up-to-date. Payment transactions are between an individual or business and their financial institution. Only the parties directly involved in the bank-client relationship would be able to know if or how transaction instructions were transmitted and if any software was used to do so. (ACH transactions are traditionally performed between business entities and their banks for regular and often recurring payments such as bill pay, payroll deposits, premium collection for insurance, etc.)
Certainly this email wreaks of the odor of a scam artist at work. May such emails are opened and forgotten about – even though the email may have placed a keylogging program or other programmatic device designed to steal your information to enable identity theft or possible account takeover of your accounts via information on your computer. THE OBJECTIVE OF THE FRAUDSTER IS SIMPLE: GET YOUR MONEY OR YOUR INFORMATION OR BOTH!
Next to stealing your money or other financial assets, the fraudster’s most valuable prize for the taking is your asset of a good, real financial identity… your good name as it were. Many crimes are built on use of a reasonably unblemished financial identity, making identity theft a long standing major black market commodity. With the advent of texting, emails and other high-tech forms of communication; coupled with our insatiable goal to make all transactions instant and easier to perform from our cell phones, PCs or iPADs — there are countless types of scams and schemes to put your financial assets and your identity at risk. And, whether you lose money outright, or you have to endure the trauma and expense of straightening out the mess caused because someone stole your identity and committed crimes using your identity, you are the victim of fraud.
So what can be done about this?
First, both at an individual and corporate level, you need to be more aware of how the fraudsters operate and how they can game the system to take advantage of you or your company.
Second, take steps to safeguard your personal and corporate information. The first ingredient is common sense: If the deal is either too good to be true or if it just doesn’t feel right, it is likely to be as you suspect it to be. If you are not sure how to best safeguard your information (or in a corporate sense if you are not sure what should be safeguarded or how to best protect it), contact us and we can point you in the right direction.
Third, if you are not sure of the parties with whom you are considering to do business in some form, engage a competent service provider to help you with your Due Diligence. (hint: just because someone used to be a police officer or is an “investigator”, this does not necessarily make them experts in performing background investigations or other forms of Due Diligence).
And the next time you get a suspicious email (like the example above) that comes either from someone you do not know or from someone you are not expecting a note from, delete it — its ok to be a little more cautious or suspicious than you might have otherwise been.