VPN’s, use them or expose your IPCI.
Back in 1993, a cartoon in the New Yorker Magazine expressed a vision of the Internet as an essentially anonymous medium.
The cartoon featured a dog peering at a video display terminal, and a caption that read, “On the Internet, nobody knows you’re a dog.”
Two decades later, the promise of the Internet as an anonymous communications medium has been shattered. Your Internet Service Provider (ISP) can monitor every e-mail message you send, every Web page to which you surf, and every chat session you initiate. If police demand this information, your ISP must turn over a record of everything you’ve done online.
Increasingly, ordinary litigants can gain access to this data as well. So can hackers and thieves looking for log-on information and passwords to steal.
But what if you could create a data stream that no one can monitor? You can, using a process called “tunneling,” in which software or hardware encrypts the data flowing between your PC and your ISP. With tunneling software, your ISP can no longer monitor the content of your online communications.
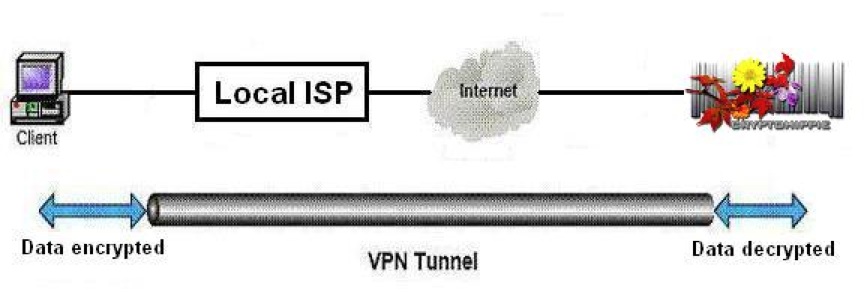
Add to tunneling something called a “proxy server” and your ISP can’t even see where you’re surfing on the Internet. All that the ISP sees is an encrypted data channel between your PC and the Web site on which the proxy server resides—that’s all. Together, tunneling and proxy service create a “virtual private network” or VPN.
VPNs also defeat another type of Internet surveillance, carried out by Web pages that record your “Internet protocol address,” or IP address. (Your IP address is a unique number and represents your publicly visible identity on the Internet.) Since the VPN acts as an intermediary between your PC and the Web site to which you’re connecting, that Web site records the IP address of the VPN, not of your PC. This lets you surf anonymously.
Here’s a graphic of how it works:
The only way anyone could recover your IP address would be by comparing the logs from the VPN and the logs from the Web site in question. That’s a little like looking for a needle in a haystack. What’s more, a well-designed VPN is configured to make it impossible to retrieve a meaningful log to connect to individual subscribers.
There are many VPN services available. We have been using the software of one company with the fun name of Cryptohippie USA that qualifies on this score. The company’s only U.S. presence is to authenticate connections to Cryptohippie servers in other countries. None of Cryptohippie’s servers are in the United States.
Another thing we like about Cryptohippie is that the founders split operations into two separate legal entities. One company handles customer data, the other encrypts the web traffic, and the two don’t ever cross paths.
I’ve used several other VPNs, and today this one works the best. For instance, a previous service I used didn’t work with my e-mail program, so I had to disconnect from it every time I wanted to send e-mail. Another service only worked with a dedicated connection and was thus impractical to use on a laptop.
The Cryptohippie “Road Warrior” VPN overcomes those problems. It takes only two mouse clicks to activate, so it’s very easy to work with. I’ve used it on dozens of wi-fi connections, and it’s connected flawlessly to all of them. Most of my Web pages now open in German, I assume because I’m connected to a server in Germany. (It’s easy enough to switch back to an English version.)
The favorite Cryptohippie story is when a friend tried to make a change to their telephone service online while logged in to Cryptohippie. The customer rep refused to help, “because we can’t tell where you are.” That’s creepy, but it shows how pervasive Internet surveillance really is, and how effective Cryptohippie is at overcoming it.
If you value your online privacy, give the Cryptohippie “Road Warrior” VPN a try.
(Pirated with permission from Mark Nestmanns’ blog)